Darkweb Search What It Is and How It Really Works

Understanding dark Web Search is essential for any organization that cares about digital risk, brand safety, or data leakage. In this guide, I’ll explain what people mean by the dark web, how legitimate discovery and monitoring happen, the real risks involved, and practical, non-actionable ways organizations protect themselves. This professional, evidence-based primer is designed for […]
Ciphbit Strikes Jimfor, S.A. in Major Ransomware Attack

Jimfor, S.A., a major player in the technology sector, has fallen victim to a ransomware attack orchestrated by the Ciphbit group. The attack has potentially exposed sensitive data, with the threat actors demanding a ransom to halt further leaks.
Akira Breaches Axelson WilliamowskyBender & Fishman

The Akira ransomware group has targeted Axelson WilliamowskyBender & Fishman, a law firm based in the USA. Over 100GB of sensitive data, including financial records and personal client information, is at risk.
Rhysida Ransomware Strikes Bellflower Unified School District

Rhysida ransomware group has targeted Bellflower Unified School District, compromising its systems and threatening to release sensitive data unless demands are met.
Qilin Strikes Productive Tool Products in Portugal

The ransomware group Qilin has claimed responsibility for a cyberattack on Productive Tool Products, a manufacturing company based in Portugal. Sensitive data may be leaked unless negotiations are initiated.
Akira Ransomware Group Targets CESO in Recent Cyberattack

The Akira ransomware group has claimed responsibility for a significant cyberattack on CESO, a leading U.S. firm in architecture and engineering. The attack threatens the exposure of sensitive employee and client data unless negotiations are initiated.
Akira Ransomware Attack on Bergman Dacey Goldsmith
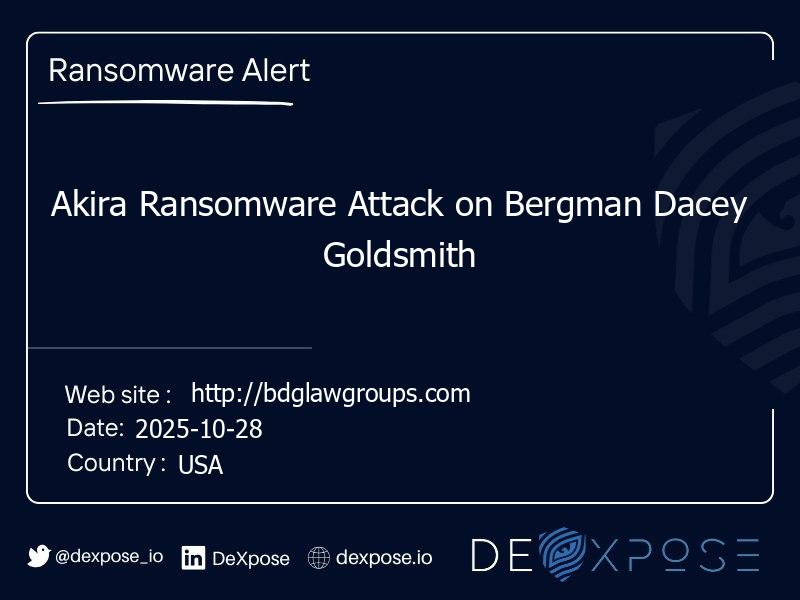
Cybersecurity alert: Akira ransomware group has targeted Bergman Dacey Goldsmith, a Los Angeles-based law firm, threatening to release 110 GB of sensitive corporate documents.
NightSpire Ransomware Attack on KONCISE COMPANY LIMITED

Thai company KONCISE COMPANY LIMITED has been targeted by the ransomware group NightSpire. With potential data leaks on the horizon, the organization faces significant cybersecurity challenges.
NightSpire Ransomware Attack Targets Sangeetha Mobiles in India

The ransomware group NightSpire has claimed responsibility for a cyberattack on Sangeetha Mobiles, a leading mobile retailer in India. The group’s extortion notice threatens data exposure unless negotiations are initiated.
Nightspire Ransomware Attack on NSC PLUS CO, LTD in Thailand

NSC PLUS CO, LTD, a Thai company, has fallen victim to a ransomware attack by the Nightspire group. The attackers have threatened to leak sensitive data unless their demands are met.
Qilin Ransomware Attack on Microbix Biosystems

Microbix Biosystems, a Canadian biotech company, was targeted by the Qilin ransomware group. The threat actors have threatened to leak sensitive data unless their demands are met.
Devman Ransomware Group Targets Ripple Flow Apps LLC
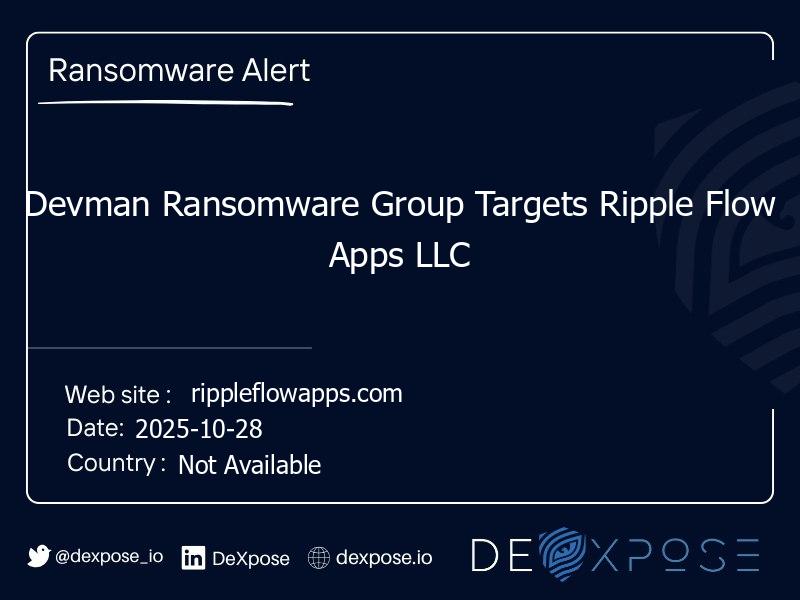
The ransomware group Devman has claimed responsibility for a cyberattack on Ripple Flow Apps LLC. The group threatens to leak stolen data unless their demands are met.