Researches, News, and more
DeXpose Blog
Deep Dive into Arkanix Stealer and its Infrastructure
Arkanix Stealer is an actively developed credential‑theft malware family that is primarily advertised on Discord, where its operators have been promoting rapid updates and new feature additions. While the initial release of Arkanix was written…
Inside Valkyrie Stealer: Capabilities, Evasion Techniques, and Operator Profile
What Is Valkyrie Stealer? Valkyrie Stealer is a C++ infostealer designed to collect credentials, system information, browser data, messaging-app sessions, and other user assets from Windows systems. It features a modular architecture, encrypted exfiltration, and…
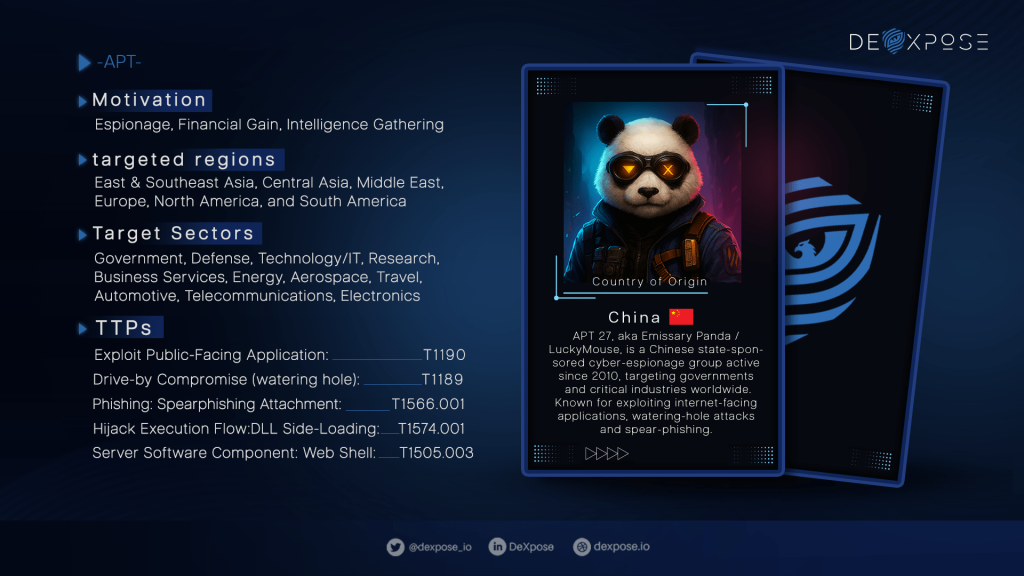
Threat Actor Profile: APT27
Who is APT27? APT27 — also known as Emissary Panda, Iron Tiger, and LuckyMouse — is a Chinese state-sponsored cyber-espionage group active since at least 2010. The group has been linked to long-running campaigns against…
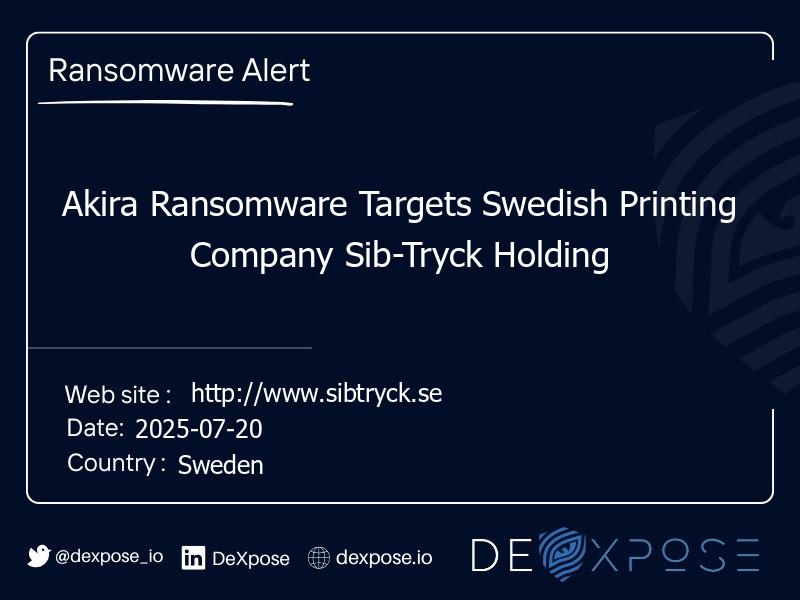
Akira Ransomware Attack on SIB-Tryck Holding Explained
Sib-Tryck Holding, a Swedish digital printing firm, has fallen victim to the Akira ransomware group. The attackers claim to have exfiltrated 45 GB of sensitive data, threatening to leak it unless contacted.
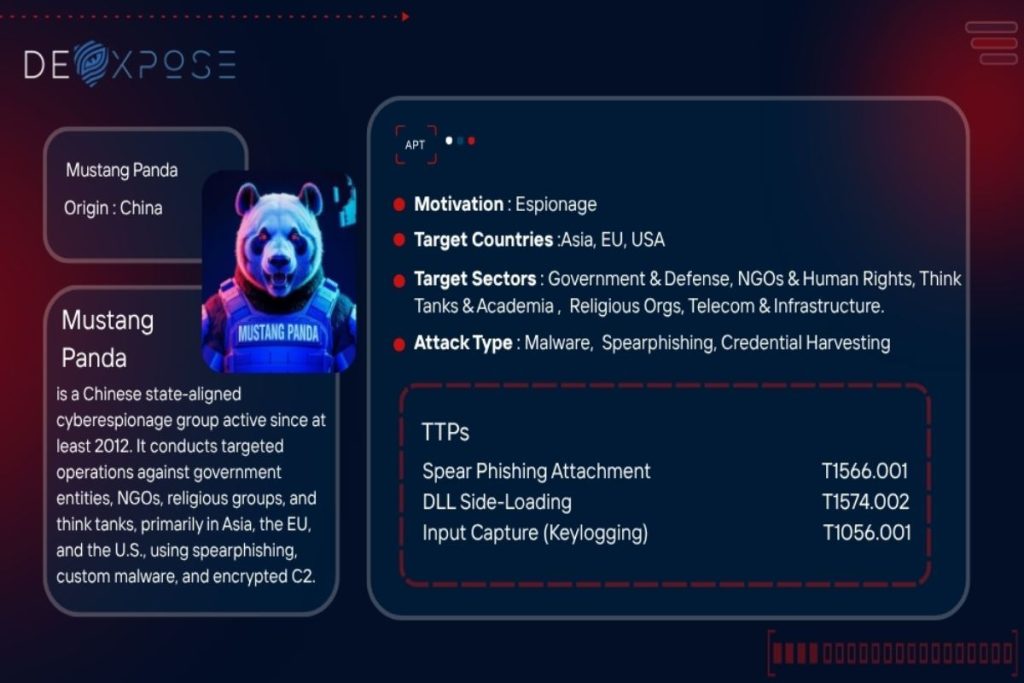
Threat Actor Profile: Mustang Panda
Mustang Panda is a highly persistent and adaptive Chinese state-linked cyber espionage group operational since at least 2012. Known by multiple aliases—including Red Delta, TA416, and Stately Taurus—this threat actor has consistently targeted entities of…
AnyDesk Clone Malware Drops Phemedrone Stealer Loader
On June 16, 2025, a suspicious domain impersonating AnyDesk — anydeske[.]icu — was reported on Twitter. The site served what appeared to be a legitimate remote access tool but actually delivered a malicious .NET loader. Further investigation…
Uncovering Kimsuky APT Infrastructure | Threat Report
Summary Recently identified previously undetected Kimsuky (also known as Black Banshee) infrastructure through advanced pivoting techniques. Using HTTP header analysis, SSL Cert and JARM fingerprinting. We uncovered several IPs and domains, many of them were…
Smishing Triad Impersonates Egypt Post in Phishing Scam
A recently observed phishing campaign impersonating Egypt Post (البريد المصري) has been attributed to the Smishing Triad, a well-documented cybercriminal group for their phishing (smishing) campaigns across multiple countries. The campaign impersonates Egypt Post, aiming to steal credentials and…
FleshStealer Malware Report – Multivector Data Theft
Introduction FleshStealer is a sophisticated, modular, and obfuscated .NET-based information-stealing malware designed for comprehensive data exfiltration from Windows systems. Its architecture is built for scale and stealth, utilizing multithreading to simultaneously run multiple data harvesting…
SalatStealer Malware Analysis and Data Theft Techniques
Introduction Salat Stealer is a stealthy malware developed in the Go programming language, designed to infiltrate systems and extract sensitive data. Once it infects a device, it gathers extensive system information, such as hard drive…
Table of Contents